Digital signature: The safety net for every e-invoice
E-invoices that aren't digitally signed can be easily manipulated without the recipient being able to verify this. Such e-invoices are easy prey for fraudsters who like to swap the bank details on the invoice.
The obligation to issue e-invoices has been in effect in Germany since January 1, 2025! There is a transition period for sending e-invoices, depending on annual turnover, until 2027 or 2028. However, there is no transition period for receiving e-invoices! Every company and every self-employed person/freelancer registered in Germany must be able to receive and validate e-invoices. An e-invoice may not be rejected, and the recipient is required to perform technical validation.
With ZEIT.IO, you can not only record time but also create and receive e-invoices. ZEIT.IO supports the two e-invoice formats ZUGFeRD and XRechnung for outgoing invoices. ZUGFeRD, XRechnung, and Peppol BIS 3 invoices can be received, validated, visualized, and stored in an audit-compliant manner for incoming invoices.
With ZEIT.IO, you can not only record time but also create and receive e-invoices. ZEIT.IO supports the two e-invoice formats ZUGFeRD and XRechnung for outgoing invoices. ZUGFeRD, XRechnung, and Peppol BIS 3 invoices can be received, validated, visualized, and stored in an audit-compliant manner for incoming invoices.
Email sending of invoices and possible attack vectors
In Germany, around 32 billion invoices are sent every year. About half of these are sent electronically. That's approximately 16 billion invoices sent via email every year. The problem is that these invoices are predominantly sent unencrypted and unsigned. This makes them very easy to manipulate.
Now, some will immediately object and say, "But we use SSL or TLS encryption to communicate with our email server." That may be all true, and you should definitely do so! However, this only secures the transport path from your email client to your email server. The email containing the invoice must be routed through several SMTP servers on the internet before it reaches the recipient's email server. And you have no control over the transport paths and encryption mechanisms between the individual email relays. These transport paths may or may not be encrypted using SSL. Furthermore, any administrator of these email relays can view and even manipulate the email in plain text. Below is a very simplified illustration showing how an email is routed through the internet and where the email is vulnerable.
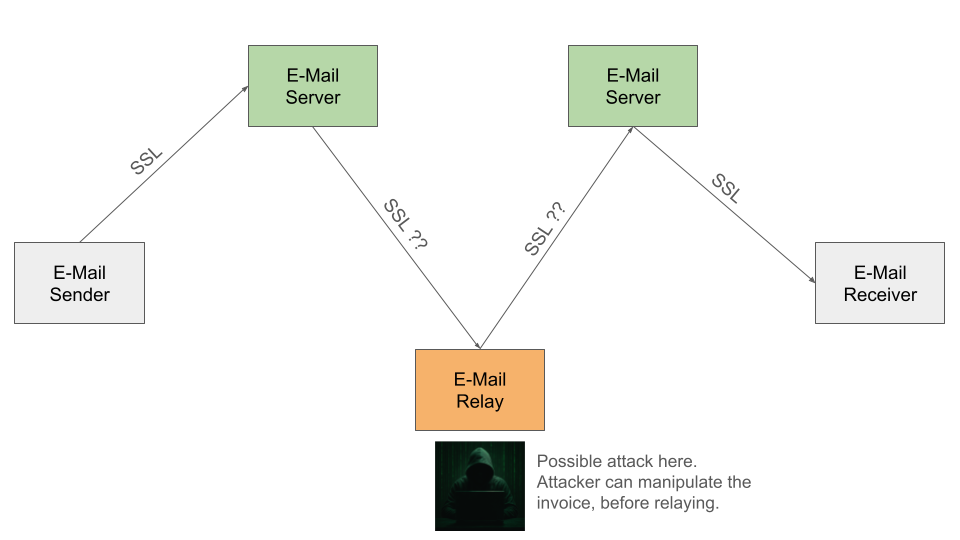 Email routing in the world wide web.
Email routing in the world wide web.
The illustration shows a classic "man-in-the-middle" attack. An actor in the middle of the transport path, through whose email relay your email is routed, intercepts the email, manipulates the invoice, and forwards the manipulated invoice to the recipient. Typically, such attacks involve swapping the bank details on the invoice. The recipient of the invoice, your customer, notices that the bank details have changed but doesn't think much of it and transfers the invoice amount to the bank account listed on the invoice. You wonder why the customer hasn't paid and eventually send a first reminder. By the time you discover that the customer paid a fake invoice, the attackers have long since fled with the money.
Now, some will immediately object and say, "But we use SSL or TLS encryption to communicate with our email server." That may be all true, and you should definitely do so! However, this only secures the transport path from your email client to your email server. The email containing the invoice must be routed through several SMTP servers on the internet before it reaches the recipient's email server. And you have no control over the transport paths and encryption mechanisms between the individual email relays. These transport paths may or may not be encrypted using SSL. Furthermore, any administrator of these email relays can view and even manipulate the email in plain text. Below is a very simplified illustration showing how an email is routed through the internet and where the email is vulnerable.
 Email routing in the world wide web.
Email routing in the world wide web.The illustration shows a classic "man-in-the-middle" attack. An actor in the middle of the transport path, through whose email relay your email is routed, intercepts the email, manipulates the invoice, and forwards the manipulated invoice to the recipient. Typically, such attacks involve swapping the bank details on the invoice. The recipient of the invoice, your customer, notices that the bank details have changed but doesn't think much of it and transfers the invoice amount to the bank account listed on the invoice. You wonder why the customer hasn't paid and eventually send a first reminder. By the time you discover that the customer paid a fake invoice, the attackers have long since fled with the money.
How do you protect yourself from fake e-invoices?
There are various ways to avoid this "man-in-the-middle" attack. One option would be to completely encrypt the email. This prevents attackers in the middle from reading the email in plaintext. However, this requires the recipient to have a password or public key to decrypt the encrypted email. This method is quite complex in practice and is rarely used.
Another option is to sign the invoice with a private certificate from a publicly trusted authority. This method is known as an asymmetric cryptosystem. If the invoice is in PDF format, as is the case with ZUGFeRD, for example, the PDF can be digitally signed. The PDF is signed with a so-called "private key." The signature also contains a hash value generated from the contents of the PDF invoice. A digital signature does not protect the file from being altered! But it can help reveal possible tampering.
If an attacker alters the invoice, the recipient can easily find out by evaluating the signature. If the invoice hasn't been altered, the signature can be positively verified. If the invoice has been altered, the hash value in the signature no longer matches the hash value of the current content, and the signature cannot be positively verified!
Therefore, as an invoice sender, you should always digitally sign your invoices, and as an invoice recipient, you should use a tool to check received invoices for their digital signature! The ZEIT.IO invoice module offers both!
Another option is to sign the invoice with a private certificate from a publicly trusted authority. This method is known as an asymmetric cryptosystem. If the invoice is in PDF format, as is the case with ZUGFeRD, for example, the PDF can be digitally signed. The PDF is signed with a so-called "private key." The signature also contains a hash value generated from the contents of the PDF invoice. A digital signature does not protect the file from being altered! But it can help reveal possible tampering.
If an attacker alters the invoice, the recipient can easily find out by evaluating the signature. If the invoice hasn't been altered, the signature can be positively verified. If the invoice has been altered, the hash value in the signature no longer matches the hash value of the current content, and the signature cannot be positively verified!
Therefore, as an invoice sender, you should always digitally sign your invoices, and as an invoice recipient, you should use a tool to check received invoices for their digital signature! The ZEIT.IO invoice module offers both!
Create signed invoices on ZEIT.IO
All PDF invoices and PDF credit notes created on ZEIT.IO have been digitally signed since August 17, 2025! We use a certificate from D-Trust, a company of the Bundesdruckerei Group. The certificate is issued to REIZ Solutions GmbH, the company behind ZEIT.IO, and is renewed annually. This is how we contribute to making the world a little safer.
If you open a PDF invoice or PDF credit note created on ZEIT.IO with Adobe Acrobat Reader, you will see that the invoice is signed. It will then look like this:
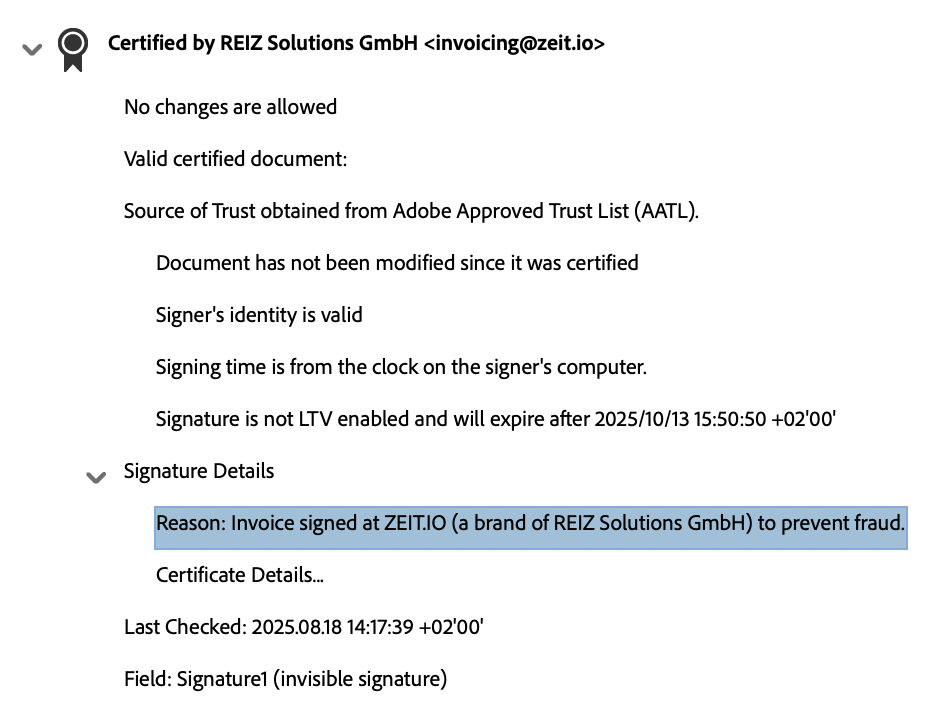 Information about the signature and certificate in Adobe Acrobat Reader.
Information about the signature and certificate in Adobe Acrobat Reader.
If you try to edit the PDF invoice in the Adobe Acrobat app, it won't be possible! Adobe recognizes the signature and therefore doesn't allow any changes to the document. Unfortunately, not all programs adhere to this standard. If you open the same file in Apple's "Preview" program on Mac OS X, no information about the signature is displayed. Many PDF readers cannot handle signatures and embedded XML files and simply ignore them.
With Apple's "Preview" program on Mac OS X, it is also possible to modify the file, despite the signature! The program can easily overwrite the bank details. However, a standard PDF is created when the file is saved. The manipulated invoice contains neither a signature nor the embedded XML file required for ZUGFeRD. Therefore, the manipulated invoice is no longer an e-invoice. And from 2027, it will no longer be a valid invoice either!
So always pay attention to this. If you receive an invoice from ZEIT.IO and it does not contain a signature, then it is most likely a fraudulent transaction!
If you open a PDF invoice or PDF credit note created on ZEIT.IO with Adobe Acrobat Reader, you will see that the invoice is signed. It will then look like this:
 Information about the signature and certificate in Adobe Acrobat Reader.
Information about the signature and certificate in Adobe Acrobat Reader.If you try to edit the PDF invoice in the Adobe Acrobat app, it won't be possible! Adobe recognizes the signature and therefore doesn't allow any changes to the document. Unfortunately, not all programs adhere to this standard. If you open the same file in Apple's "Preview" program on Mac OS X, no information about the signature is displayed. Many PDF readers cannot handle signatures and embedded XML files and simply ignore them.
With Apple's "Preview" program on Mac OS X, it is also possible to modify the file, despite the signature! The program can easily overwrite the bank details. However, a standard PDF is created when the file is saved. The manipulated invoice contains neither a signature nor the embedded XML file required for ZUGFeRD. Therefore, the manipulated invoice is no longer an e-invoice. And from 2027, it will no longer be a valid invoice either!
So always pay attention to this. If you receive an invoice from ZEIT.IO and it does not contain a signature, then it is most likely a fraudulent transaction!
Validate signed invoices on ZEIT.IO
You can receive incoming invoices in the ZEIT.IO invoice inbox. Either via the e-invoice mailbox or simply by dragging and dropping a file onto the invoice inbox. If the file is an e-invoice, ZEIT.IO will also validate and visualize the invoice. Validation includes checking for technical correctness, compliance with syntax and the official code lists, AND checking the signature, if one is present!
If the file does not contain a signature, this will now also be displayed. It will look like this:
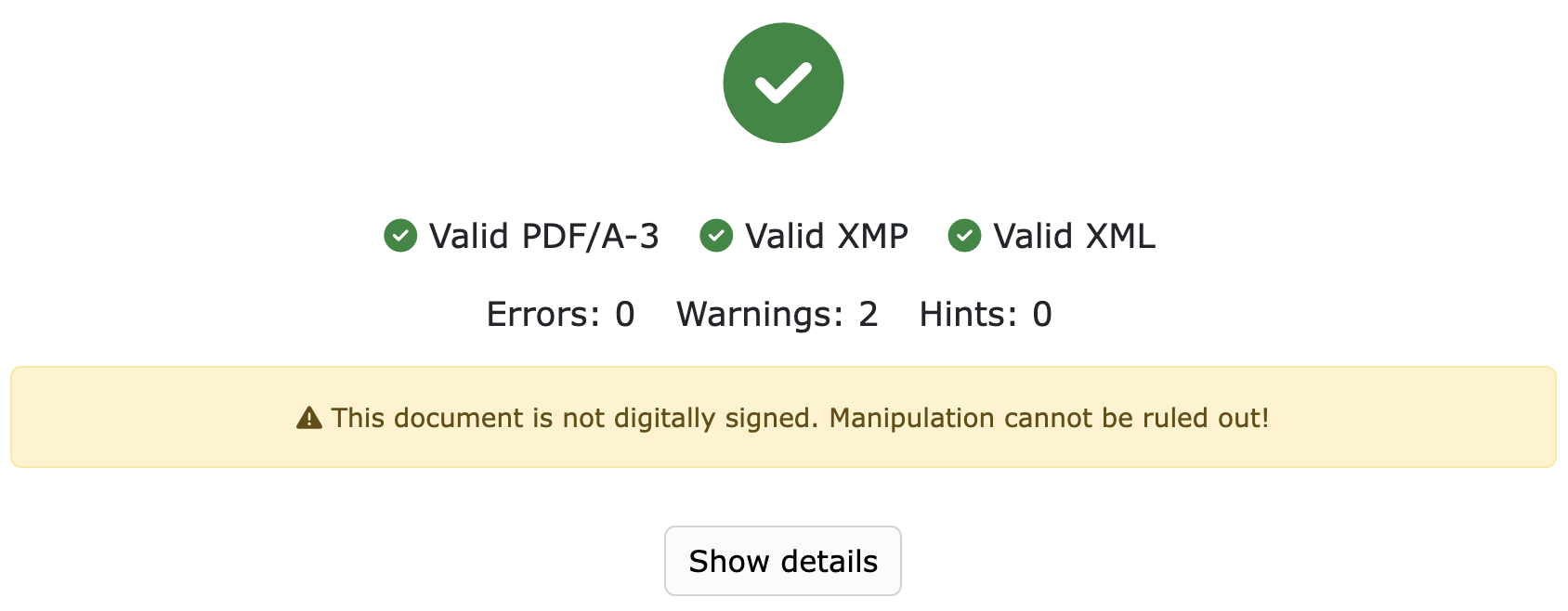 Valid e-invoice without digital signature.
Valid e-invoice without digital signature.
An unsigned e-invoice can, of course, be valid. However, tampering cannot be ruled out.
If the file is digitally signed but has been altered, ZEIT.IO will mark the invoice as invalid.
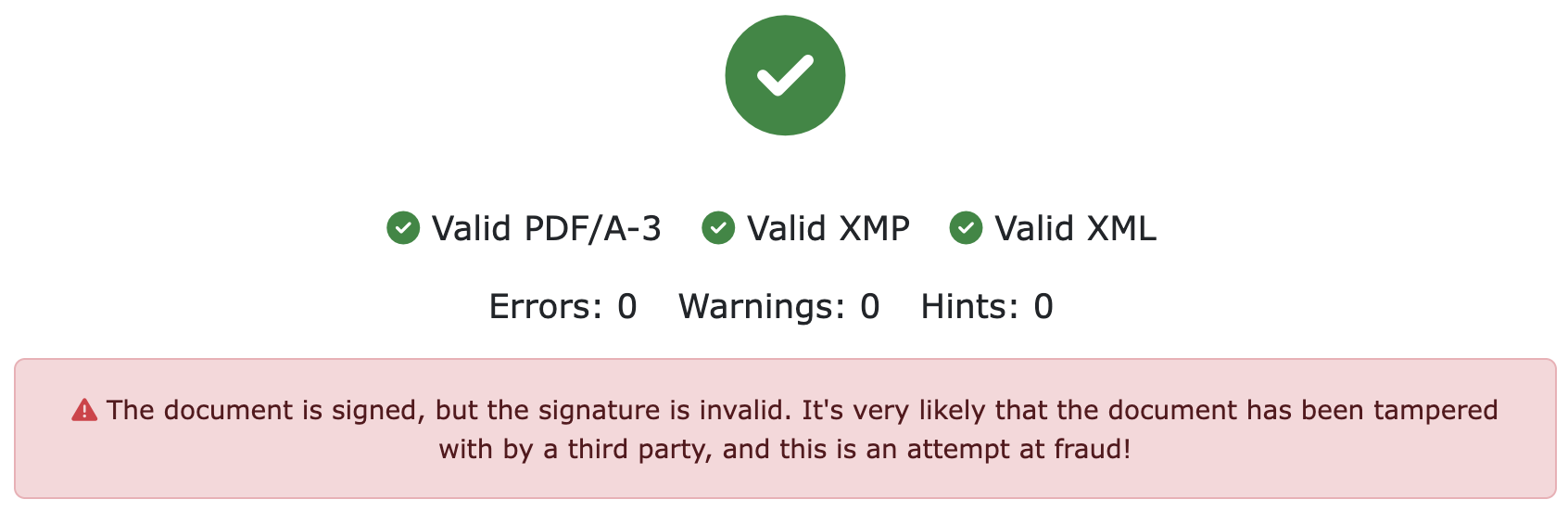 Warning on ZEIT.IO that the e-invoice has been manipulated and is likely a fraud!
Warning on ZEIT.IO that the e-invoice has been manipulated and is likely a fraud!
If the digital signature of the e-invoice can be positively validated and the invoice is also syntactically correct, this will be displayed here.
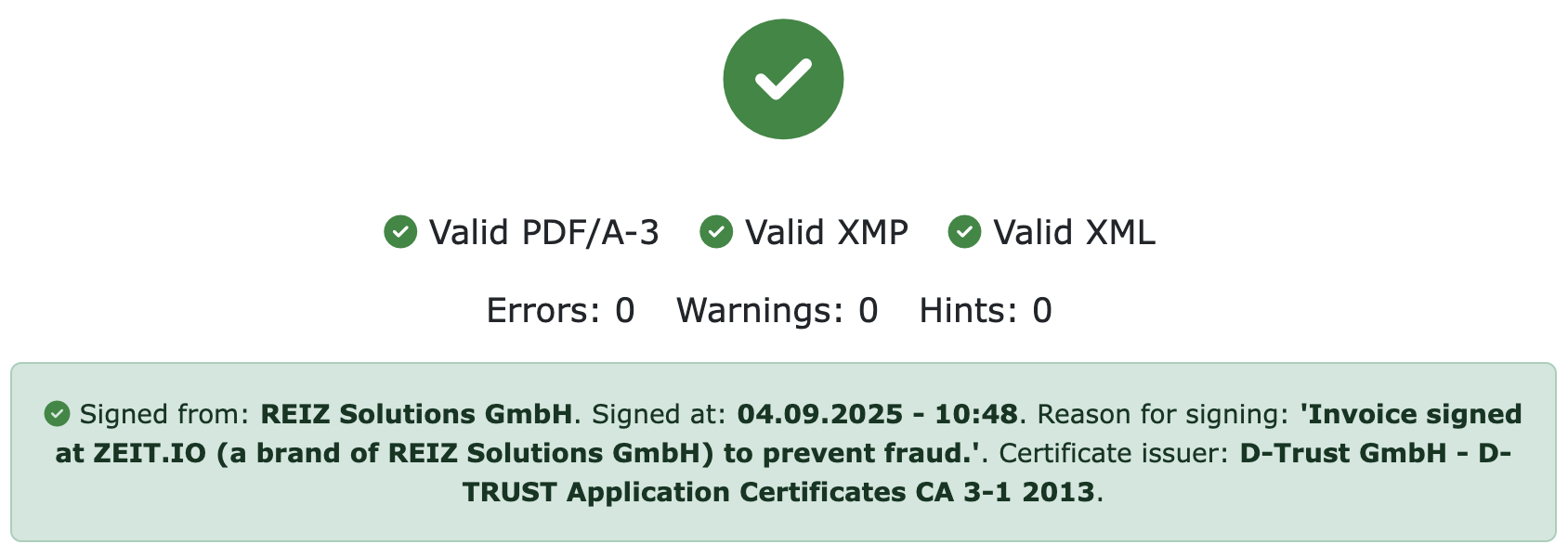 Digitale Signatur einer E-Rechnung konnte positiv validiert werden.
Digitale Signatur einer E-Rechnung konnte positiv validiert werden.
The example above also shows which company signed the file, when, for what reason, and who issued the certificate for signing. The last part, "Certificate Issuer," is especially important! You should always ensure that the certificate was issued by a known, trusted authority. Self-issued certificates are not trustworthy!
If the file does not contain a signature, this will now also be displayed. It will look like this:
 Valid e-invoice without digital signature.
Valid e-invoice without digital signature.An unsigned e-invoice can, of course, be valid. However, tampering cannot be ruled out.
If the file is digitally signed but has been altered, ZEIT.IO will mark the invoice as invalid.
 Warning on ZEIT.IO that the e-invoice has been manipulated and is likely a fraud!
Warning on ZEIT.IO that the e-invoice has been manipulated and is likely a fraud!If the digital signature of the e-invoice can be positively validated and the invoice is also syntactically correct, this will be displayed here.
 Digitale Signatur einer E-Rechnung konnte positiv validiert werden.
Digitale Signatur einer E-Rechnung konnte positiv validiert werden.The example above also shows which company signed the file, when, for what reason, and who issued the certificate for signing. The last part, "Certificate Issuer," is especially important! You should always ensure that the certificate was issued by a known, trusted authority. Self-issued certificates are not trustworthy!
Conclusion
The digital signature is the safety net for every e-invoice!
ZEIT.IO signs outgoing invoices to protect them from tampering and increase trust! Digitally signed incoming invoices are verified for authenticity in the incoming invoice process, and tampered files are immediately exposed! With ZEIT.IO, you're on the safe side!
ZEIT.IO signs outgoing invoices to protect them from tampering and increase trust! Digitally signed incoming invoices are verified for authenticity in the incoming invoice process, and tampered files are immediately exposed! With ZEIT.IO, you're on the safe side!